comprehensive data logging, analysis, and packet capture solutions, built from the ground up for you


Portable / Deployable Data Recording Server Products

Software OEM Services
We optimize software system performance (eg. for data ingestion rate, etc.) running on field-deployable hardware platforms, for 3rd party software provided by our Original Equipment Manufacturer (OEM) customers.
Some of the services we provide include:
- Detailed throughput analysis including improving data ingestion rates in data recording use cases
- BIOS optimization settings
- storage partition mods
- CPU/Thread core mapping
- CentOS/RedHat Linux configuration optimizations
- VM configurations
- recommended adjustments / improvements to customer source code
- 3rd party source code maintenance
We thoroughly document operating instructions for how users can achieve optimum performance in the field.

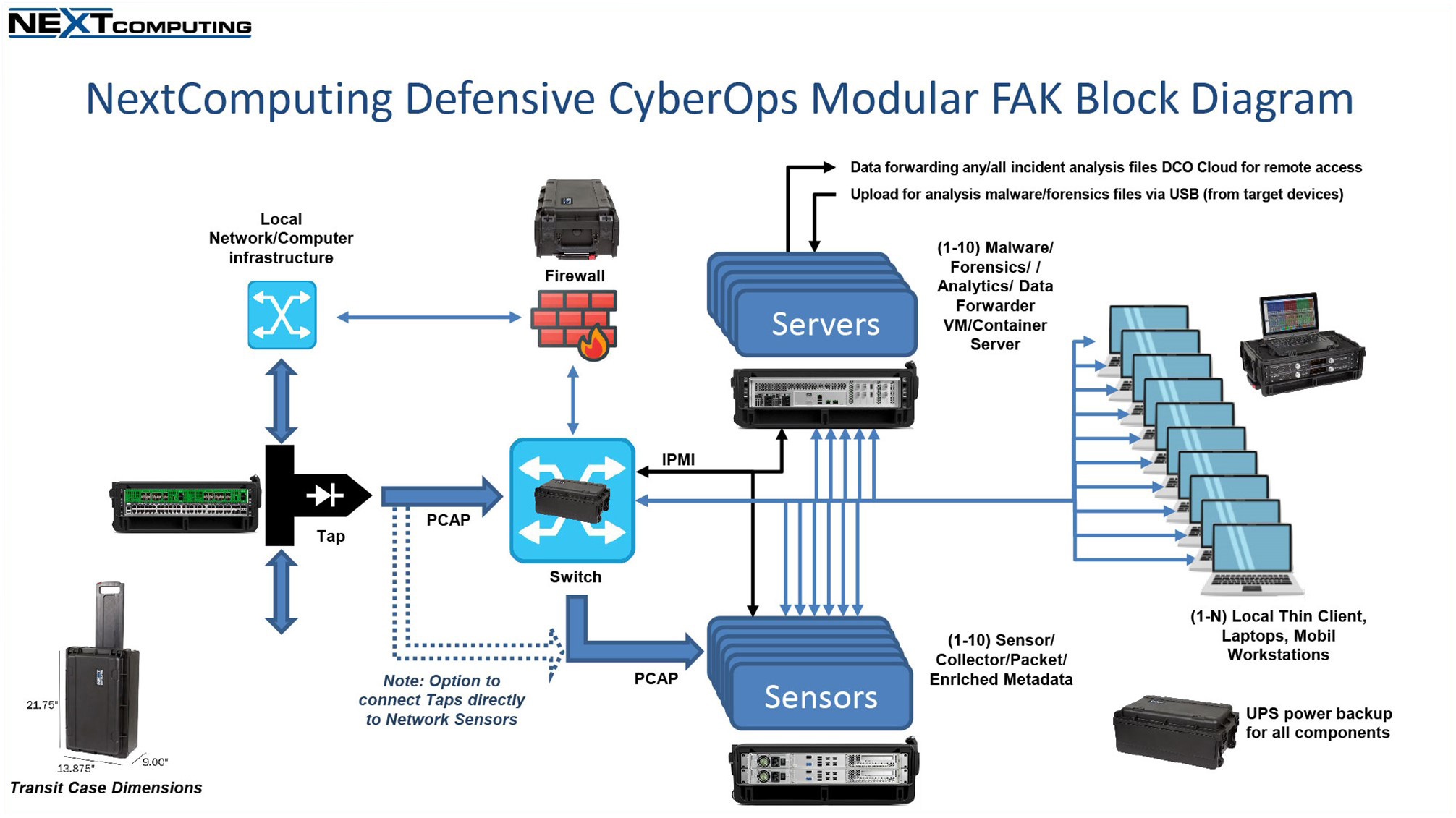
Fly-Away Kit (FAK) Systems
We bundle deployable appliance(s) and accessories, with multiple 3rd party software packages as complete mobile solutions. We provide custom FAKs, and also offer specific standard FAKs for use cases like
- Pentest
- Digital Forensics
- Servers for remote data-collection / data-forwarding
- Network Sensors for CPT threat-hunting
We specify and support 3rd party software for all of these FAKs, install them in appropriate VMs etc, and provide complete documentation and end-user operating instructions and training, along with ongoing software patch/update services and QA/regression testing and logistics services.
Software Framework Products

The NextComputing Advantage

Experience
The key value-add for NextComputing is our unique experience manufacturing and optimizing the performance of integrated hardware/software systems for mobile deployment.
Deployable systems have special challenges for maintaining top software performance, while accommodating real hardware platform constraints, and difficulties of field deployment for reliability, support and rapid change. In addition, personnel turn-over within mobile teams requires special attention for technical documentation and operating instructions, as well as consistent QA testing and logistics management.
We understand agile software development, and have been committed to this concept in our existing businesses because:
- Agile development is a key success factor for our long-standing OEM services business that supplements the underlying hardware platform products targeting mobile deployment.
- Our software framework products are tools specifically developed to facilitate agile software development in the challenging application of real-time packet capture and DPI forensics. Agile development is essential because of changing OEM requirements and variable hardware platform constraints.

Support
The NextComputing software and systems engineering team can assist you with your open source implementations for network data logging, using our proven OEM services methodologies to optimize performance on your specific enterprise or deployable platform or ideally one of our various form factor deployable NextComputing platforms , and providing sustainable long term support and software feature upgrades in coordination with your CPT, SOC and NOC teams.
As with our Fly-Away Kit business, we will quickly acquire and diagnosis issues with 3rd party software, and then manage, document, support, optimize and continually update those software packages over time.


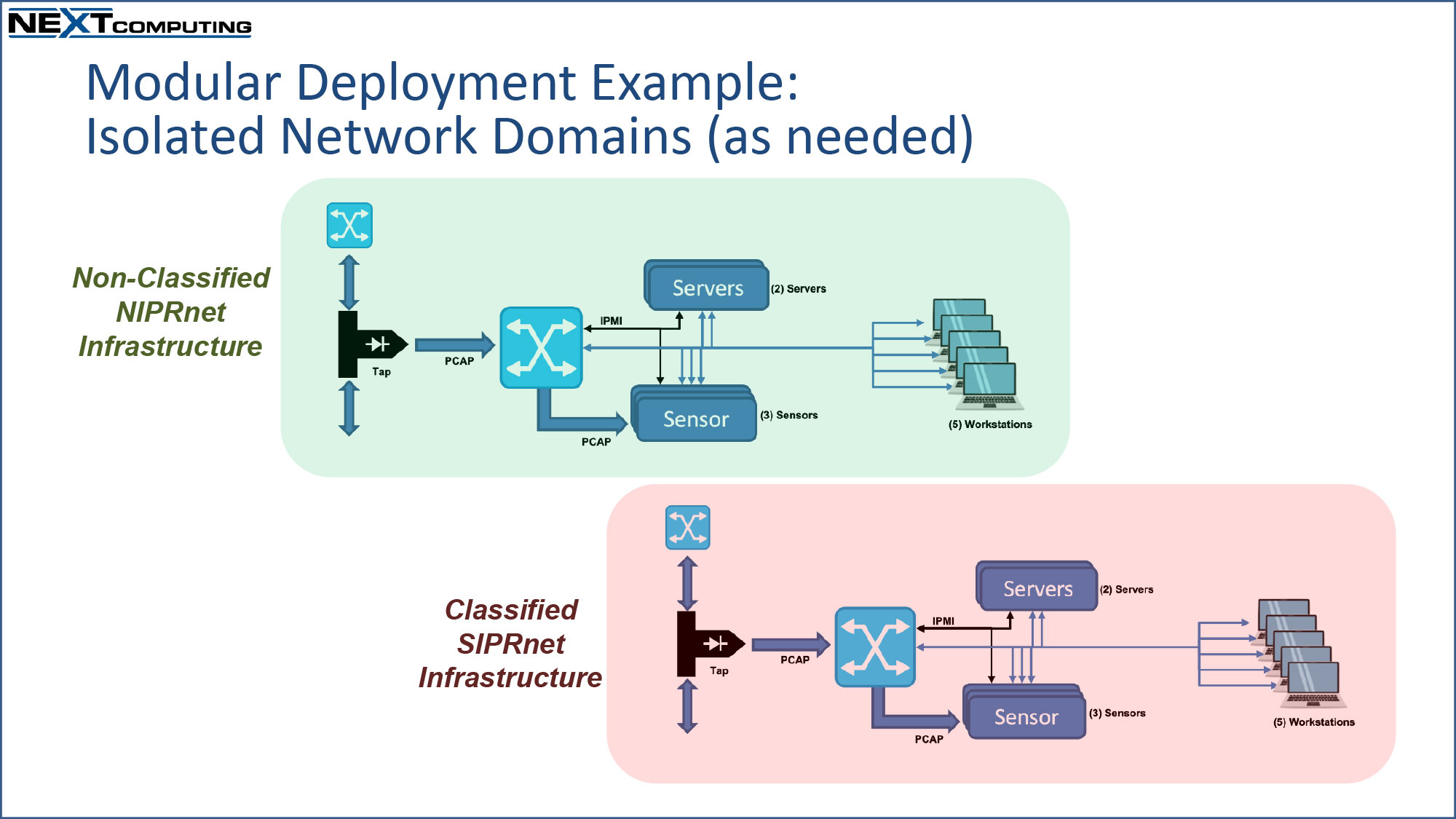
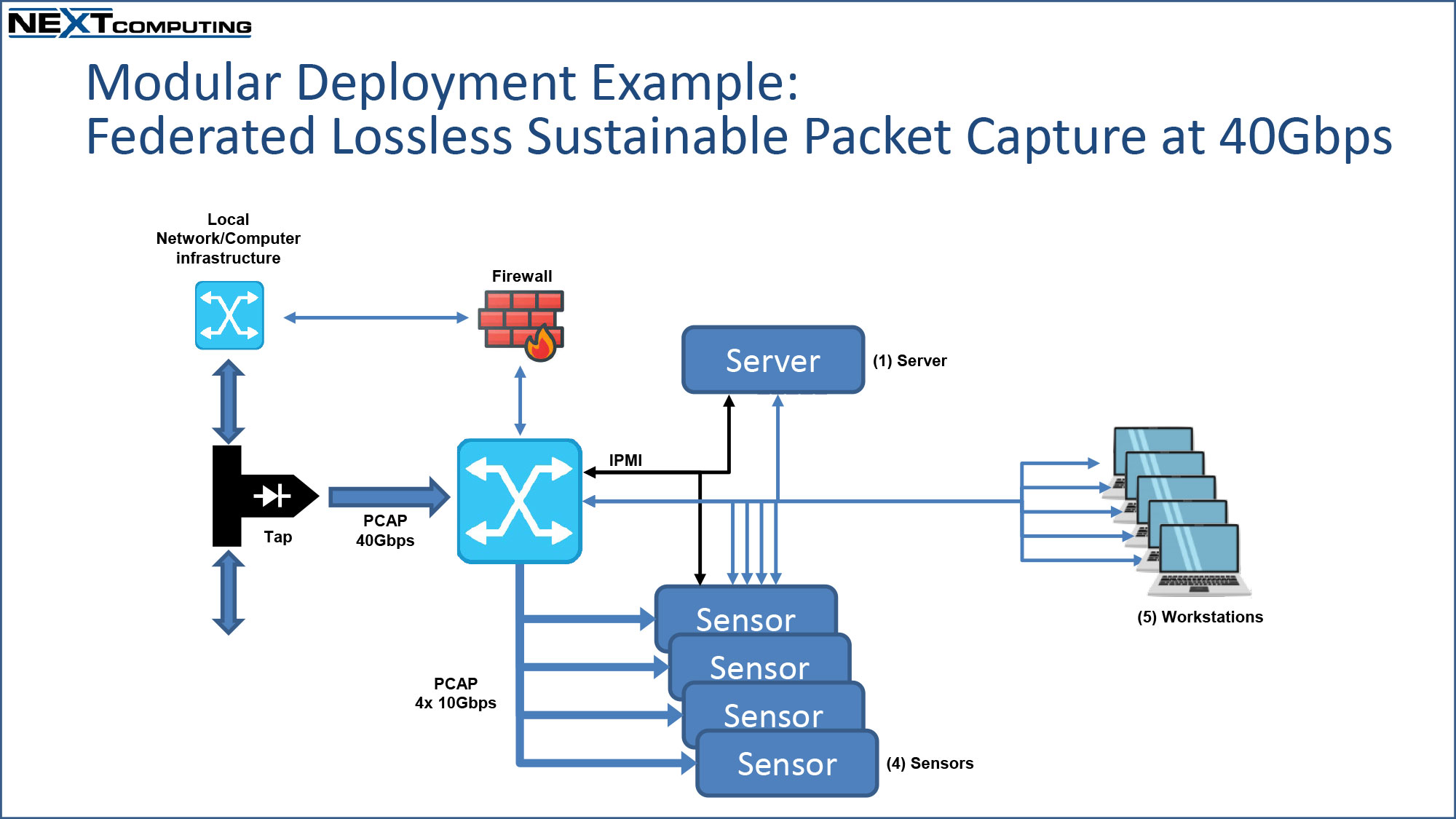
Use Case: Modular Fly-Away Kit

More About NextComputing Capabilities

Cyber Software Development Experience / Capabilities





Configuration Management Capability

Air-Gap Updates / Support Enhancement Services
Software installation and regular software version updates / patches are always a challenge for cyber operations within a restricted air-gap environment. This is especially true for mobile FAK systems that contain many diverse software tools — both commercial and free or open-source FOSS software, each with their own update schedule. NextComputing has developed unique capabilities to support FAKs deployed across air-gaps. NextComputing engineering support services will bundle multiple software updates together so that all integrated software packages can be brought to current version with a single operating procedure. Software updates with clearly documented instructions will be provided via a secure ShareFile, such that cleared support personnel (either the customer team, or a cleared/certified technical support partner of NextComputing) have instant access to download updates and instructions for removable media to carry across the air-gap. Within the air-gapped zone, support personnel will be able to update all FAK units from a central point, using the “Federation Manager” feature of the Packet Continuum software framework.
Certain FAK software tools, including threat intelligence resources with streaming data services or internet-based threat query access, will not operate as-is in an air-gap environment. NextComputing has experience working with customers to minimize operational complexities and optimizing the value for cyber operations of software tools within a restricted air-gap zone. Sometimes the solution is to bring the threat data base into the air-gap zone. When this is not possible, NextComputing can assist with custom software and/or special operating procedures. NextComputing has extensive experience with FAK hardware, software tool suites in air-gap operation for multiple customers.

Additional Capabilities
- Ability to improve ingestion rates, reduce latency and response times, reduce footprints, enhance usability aspects
- Our modular, component-based development method is based on the fundamental Unix philosophy of creating small components that can be combined in a way to get the problem solved
- Strong performance benchmarking and optimizations for packet ingestion and metadata processing
- Strong ability to debug and offer timely resolutions
- Our team possesses deep understanding of all aspects of application development, respect for frameworks and languages, and the need to keep our platform open and extendable.
- Processing PCAPs in an appropriate format understood by Wireshark and other tools
- DPI, alerts, and metadata converted to JSON format for optimal efficient data ingestion into Elastic
- To support agile development methods, we are passionate about our work and success outcomes for customers — and open to various programming languages or frameworks including a deep understanding of both Suricata and Zeek. We can recommend the appropriate framework based on customer needs.
- Augmentation, enrichment and custom-mapping of DPI data from Suricata and/or Zeek
- We have components and workflows built using languages such as C, C++, Rust, Python, Java, Javascript, React, KQL, Shell scripting
- We have strong proficiency in understanding deeply open-source projects
- We have embedded free version of ELK stack into our framework and improved its scalability
- One of the biggest clients of Elasticsearch (licensed version) for other projects has said how well we are extending the capabilities of the free version, when they noticed that we have managed to store 56 billion documents on a single Elastic node
- We are one of the earliest adapters of DPDK. We have DPDK running on various systems and NIC architectures — each with different configurations and resources